Information security policy management
- Information security risk management framework
In response to the rapid changes in the technological environment and the diversification of business development, and to effectively protect the company and customer operational information while providing sound information security governance to safeguard the information assets of the company and its relevant stakeholders, the company established an Information Security Committee in 2022. The committee implemented the ISO 27001 information security standard and obtained relevant international information security certifications, which were verified and passed on May 30, 2023, with the certificate remaining valid.

- Information Security Management Organization
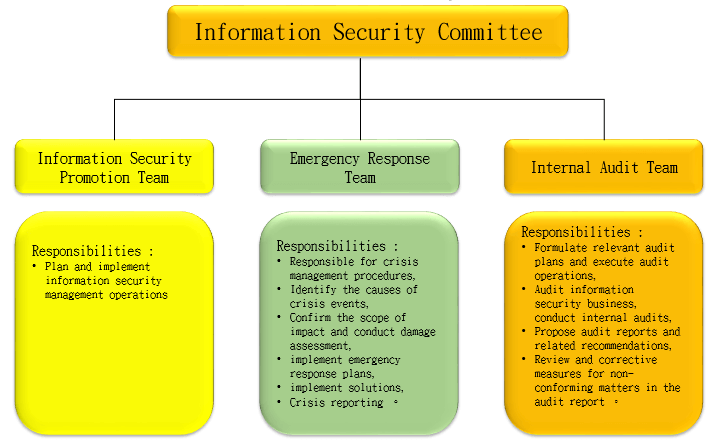
In order to improve the company’s overall information service management performance, ensure the consistency of information and business needs, and effectively manage information security work, the Information Security Committee is established. The deputy general manager of the Management Department is the chairman, the Executive Secretary is the top director of the information department, and the Information Security Promotion Team, Internal Audit Team and Emergency Response Team are established under the Information Security Committee. Review and revise the Company’s information security policies and specifications in accordance with the Company’s operational needs, changes in laws and regulations, customer security needs, technological changes and acceptable risk assessments.
Organizational operation mode – adopt PDCA (Plan-Do-Check-Act) to ensure that our reliability goals are achieved and continuously improved. The Audit Office conducts audits in accordance with the annual audit plan and reports to the Board of Directors.
- Information Security Policy
- Establish an information security management organization to be responsible for the establishment and promotion of information security systems.
- Regularly implement information security education and training, and publicize information security policies and related implementation regulations.
- Establish a management mechanism for host and network usage to coordinate the allocation and utilization of resources.
- Before constructing new equipment, risk and safety factors must be taken into consideration to prevent situations that endanger system security.
- Establish physical and environmental safety protection measures for the information computer room, and perform relevant maintenance on a regular basis.
- Clearly regulate the usage rights of network systems to prevent unauthorized access.
- Develop an internal audit plan for the information security management system, regularly review the usage of all personnel and equipment within the information security management system, and formulate and implement corrective and preventive measures based on the audit report.
- Formulate operational continuity management regulations and conduct practical exercises to ensure the continuous operation of this business.
- Maintain information security and comply with relevant information security management regulations.
- Information security management system documents should have clear management specifications.
- Invest resources in information security management
To protect against emerging malicious threats, the company strengthens information security-related construction.
- Establish a network entity isolation and supervision mechanism to effectively prevent external threats
- Establish an anti-virus system and an active defense alarm platform to strengthen monitoring of known and unknown information security threats.
- Build a server backup platform and multiple backup systems.
- Continue to implement information security education and case promotion, include it in required employee education and training courses, and enhance employee security awareness.
- Timely revise various risk factors and response actions to strengthen the company’s internal information security.
- Convening of various information security meetings, information security education and training, and information security drills: In 2024, 2 information security management review meetings, 2 information security risk assessment meetings, 1 information security internal audit planning meeting, 16 information security monthly and quarterly report meetings, 2 factory-wide social engineering drill, and Publicity and training on factory information security cases 16 times.
- The amount of information security related expenses invested by the company in 2024 is NT$3,807k.
- Information Services Continuing Operations Plan
In order to ensure that information services can minimize the impact on business and resume operation in the shortest possible time by taking appropriate response measures in the event of sudden major disasters, the Company has formulated a continuous management plan for information services, and conducts annual drills and reviews to maintain resilience and the company’s continuous operation.


